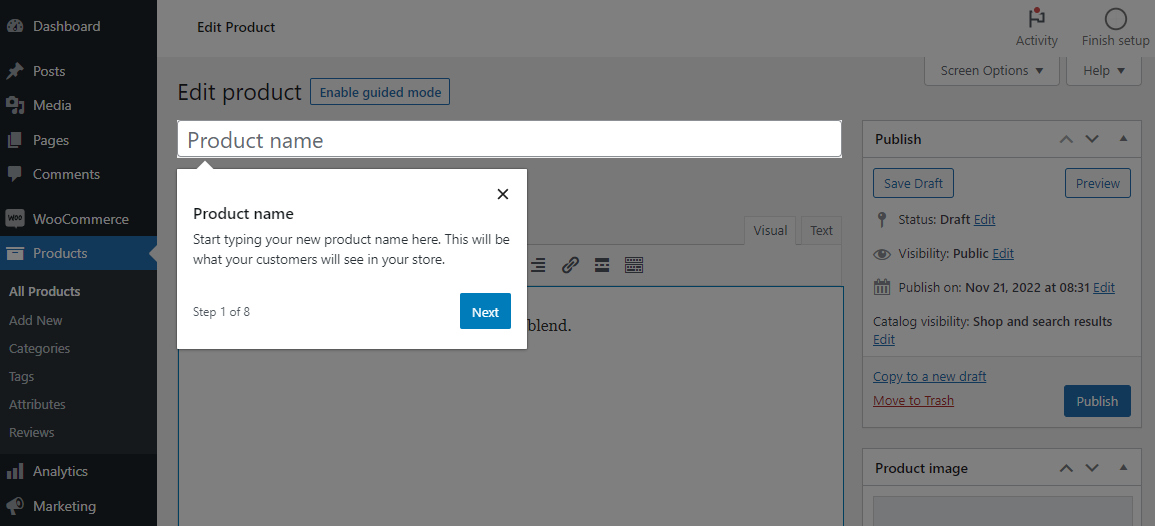
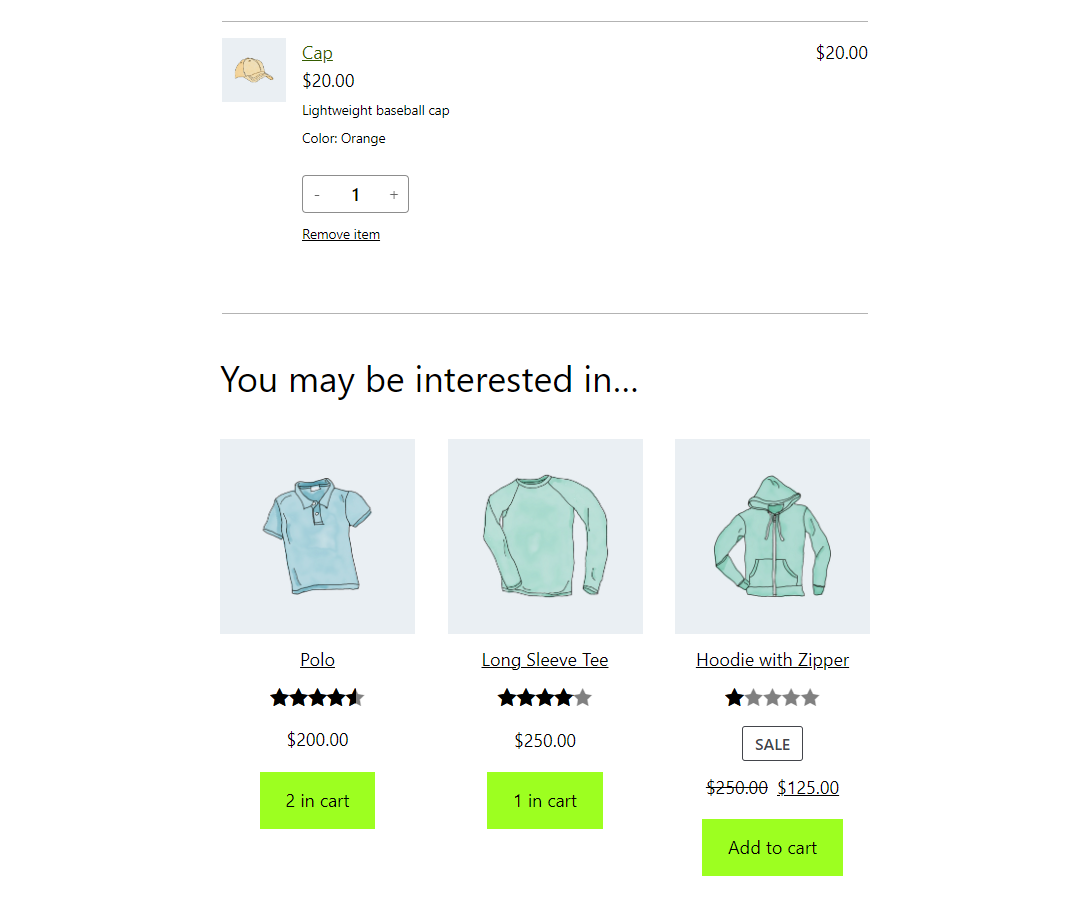
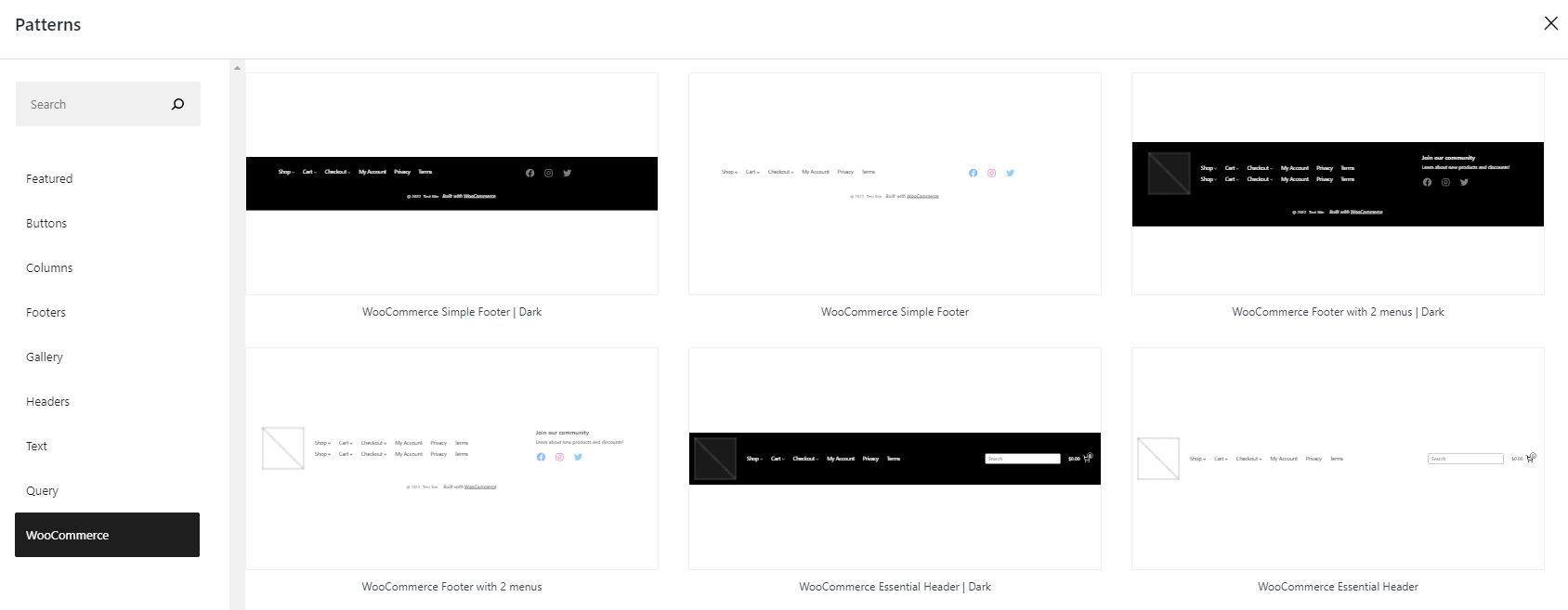
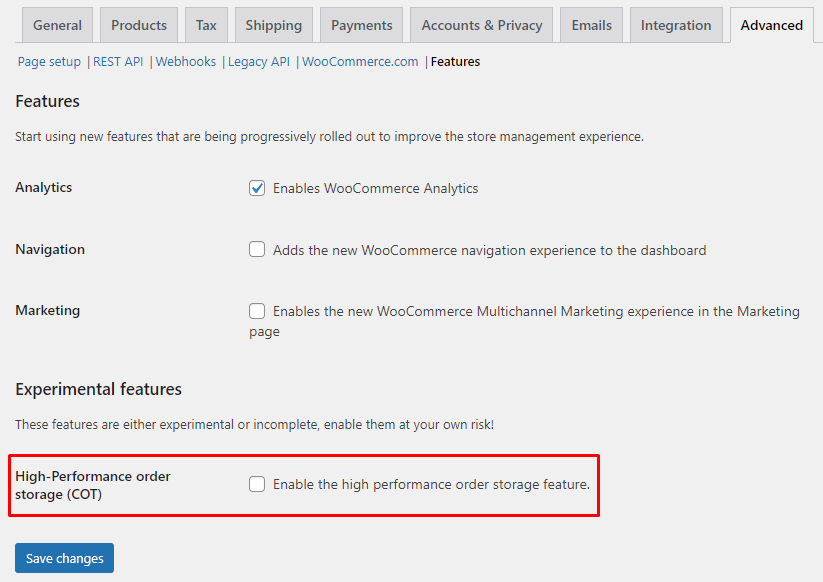
Tech Beat by Namecheap – 9 December 2022
A younger generation, known as Gen Z, is changing the online world, just like their predecessors, the Millennials. As Gen Z customers express their different desires, web-based superpowers that were highly popular a few years ago have been replaced by new favorites. An obvious illustration of the continuing alteration of the online space is dating applications, where blind dating apps are attempting to reform how people come across their prospective partners. This week’s lead story dives into how Gen Z is embracing this technology.
In other news
- Soon Airplane Mode won’t be required in the EU. Ever finish a flight only to realize worriedly you forgot to turn airplane mode on? This will no longer be an issue if you’re in the EU. According to Gizmodo, the European Commission has ruled to allow airlines to provide 5G technology on flights. On 5G-equipped flights, passengers will be able to make phone calls, access apps, and stream videos and music. This is in contrast to the slow Wi-Fi available on some flights currently. To achieve this, airlines will route calls, texts, and data through a satellite network connecting the plane to mobile networks on the ground by using special network equipment called ‘pico-cell.’
- Official encryption keys used to approve malicious Android apps. Wired reports that a number of digital certificates used by Android manufacturers to verify an app’s authenticity have been compromised. Approved Android manufacturers, such as Samsung, play a key role in tailoring and securing Android’s OS for their devices. So for their platform certificates to fall into the wrong hands is a worrying development. Malicious actors could potentially use the certificates to change app permissions to do things like collect user passwords and access entire camera rolls. Google has since caught the issue, stating it has not found evidence of malware on the Google Play Store. However, third-party app stores may be affected.
- Killer robots shelved for now. Last week we reported that San Francisco had proposed using robots in police matters, including giving them the ability to use deadly force. This week, after a huge public outcry, the city’s Board of Supervisors backtracked on this plan, according to Wired. After reluctantly voting for the policy, Gordon Mar, a member of the Board, noted, “I’ve grown increasingly uncomfortable with our vote & the precedent it sets for other cities without as strong a commitment to police accountability. I do not think making state violence more remote, distanced, & less human is a step forward.”
- Eadburg was here. Researchers at the Bodleian Library at Oxford discovered the Old English female name Eadburg scratched onto the pages of an eighth-century manuscript. As The Guardian reports, these researchers used new technology to capture 3D images of the surface of the pages of the English manuscript, a Latin copy of the Acts of the Apostles. This discovery is remarkable because it’s the first time the technology has been used to find previously unseen writing. It’s also noteworthy because, as Jessica Hodgkinson, a Ph.D. student University of Leicester, noted, “there are only a limited number of surviving early medieval manuscripts which contain clear internal evidence of a woman having created, owned or used them.” Researchers also found crude tiny drawings tucked away on the pages.



- Electric bikes saving African wildlife. In a new weapon against illegal poaching, rangers are now turning to e-bikes as a way to track and stop poachers in Mozambique’s national parks, Wired reports. Because these bikes are almost silent, anti-poaching teams can now catch poachers in the act. And these efforts have a huge impact on the ecosystems of these parks, saving hundreds of animals, including large numbers of suni, red duikers, and blue duikers, all species of antelopes that serve as food sources for predators such as eagles, leopards, and pythons. As funding becomes available, more parks across the continent may start using them to save endangered rhinos and other species.
- Beware of apps offering quick loans. Nearly 300 different predatory loan apps on the Google Play and Apple App stores had been downloaded by 15 million users before the app stores pulled them. According to The Register, these apps offered great deals on loans but included high-interest rates and hidden fees, and required users to agree to share sensitive personal data, including their text history, photos, contact lists, and more. Security researchers at Lookout discovered the scams, in which cybercriminals behind the apps used this data to extort users, demanding repayment within days or the data would be leaked publicly. Lookout points out that there may be other apps out there with similar practices, and includes more details on the scam as well as ways to protect yourself.
Tip of the week: How to keep up with online trends and reach Gen Z
With the digital revolution in full swing and the average person spending more hours online, keeping up with online trends is essential for staying ahead of the competition. As Gen Z comes of age, it is important to understand their online habits, preferences, and motivations in order to reach them effectively.
If you want to reach and engage with Gen Z, here are some tips to keep in mind.
- Set Google Alerts for unfamiliar trending topics. Stay up to date on online trends. When you hear about a trend or an unfamiliar influencer, set Google Alerts for new stories, and get up to speed.
- Leverage AI and machine learning. Gen Z is comfortable with and interacting with technology. Create AI-driven news feeds on Pocket and Flipboard that follow stories popular with Gen Z, then read the headlines daily to look for trends and patterns.
- Be authentic and transparent. Gen Z will appreciate being given an inside look at your web team or brand. Use visitor surveys to discover what aspects of your company younger people are most curious about.
- Listen to podcasts. Free streaming podcasts are a vast goldmine of Gen Z data because many of them are created by younger people, for younger people. One option is the aptly named Keeping Up With Gen Z, recorded at the Stavros Niarchos Foundation Library Teen Center. Listen to a few episodes, and get first-hand intelligence on Gen Z trends.
Source link