How Hostinger’s Customer Success Team Empowers Vitor’s No-Code Software Development Services
Customer experience is one of the most crucial factors to look out for when trying out a web hosting service. After Vitor’s website went down due to a mishap by his previous provider and no clear explanation was provided, he decided to search for a better alternative. Learn how this incident led Vitor to Hostinger and why he chose to stay with us.
The Background
Vitor Braga is a software developer from Brazil. With nearly 17 years of experience, he knows how important it is for small to medium-sized enterprises to have the right tools to operate their businesses.
However, creating software that suits all your needs is no easy task. You must either have the money to hire a software developer, which can be expensive, or the skills to build the application yourself, which can take a long time to master.
Vitor launched a startup that tackles this exact problem. VTB Solutions specializes in no-code, AI-powered services that help businesses create software without having any technical expertise. Vitor and his team call themselves the ‘solution developers.’
To market his business and accomplish its mission, Vitor needed a website.
The Challenge
To launch his website, Vitor decided to purchase a hosting plan from a popular provider in Brazil, which he used for quite some time.
Unfortunately, the company’s slow customer support and lack of communication became a major source of frustration for Vitor.
“We had a very, very big problem with the DNS configuration. One day, the provider just reset our DNS settings without informing us. This made the site inaccessible to our clients and us. We asked their support, ‘What happened?’ And their only reply was, ‘We had a problem with your website.’ We got a lot of answers like that when we were with them, ”Vitor said.
When the same issue happened again one week later, Vitor decided it was the last straw. He left his then-provider and began searching for a better alternative. He wanted one with responsive customer support, an excellent reputation, and a reasonable price.
The Solution: Migrating to Hostinger
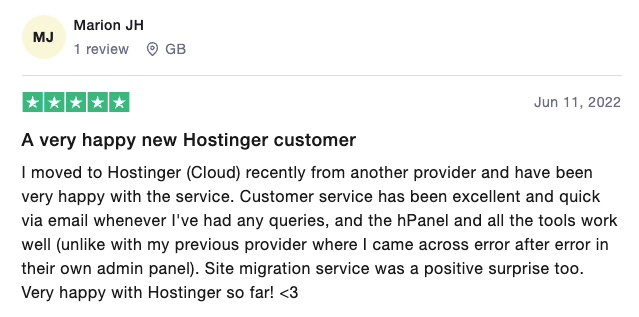
When Vitor was reading reviews about web hosting services, Hostinger was listed as one of the top picks for the best value for money.
On ReclameAqui, a popular Brazil-based complaint website, our services are scored 8.7 out of 10with a 93% success rate in solving customers’ problems. We also have an Excellent rate of 4.3 out of 5 stars on Trustpilot. Such reviews convinced Vitor to try our web hosting.



After looking at the plans, Vitor went with Hostinger’s Premium Shared Hosting. It offers unlimited bandwidth and 100 GB of SSD storage, which is plenty of space for running a small to a medium-sized business website.
At first, he planned to test five hosting providers and compare them side by side. However, Vitor was so impressed with Hostinger that he no longer needed to check out the other hosts.
When asked what made him stay with us, he said our Customer Success team was a major contributing factor.




At Hostinger, clients can get 24/7 customer support via live chat and email on any day of the year. Our Customer Success agents also live across different time zones and speak over ten languages.
What’s more, we have an extensive knowledge base that offers answers to frequently asked questions about using our services. If you’re looking for how-to guides to build your online presence or configure your website, our vast library of tutorials can help you out.
Vitor also shared another feature that surprised him – the easy SSL configuration.
After transferring his domain name, he was able to purchase and install a lifetime SSL certificate automatically on the control panel – no technical know-how was necessary. Vitor can also feel safe knowing his certificate will never expire, as it will encrypt all client-server communications for an unlimited period.
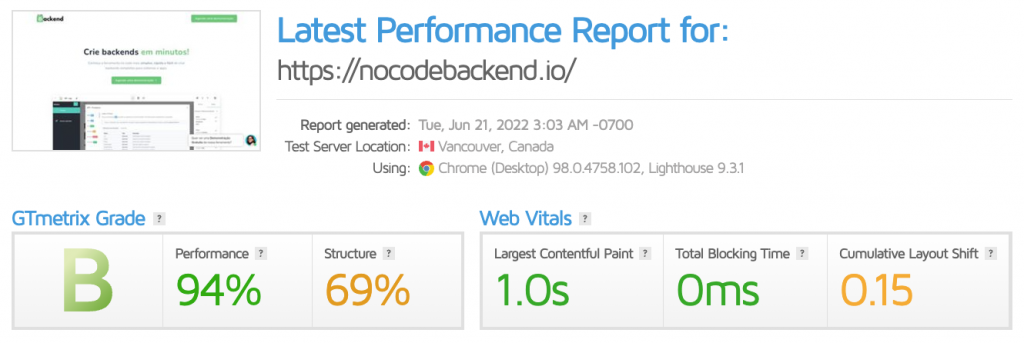
Today, Vitor’s websites are up and running smoothly at Hostinger. In fact, the latest GTMetrix test gave his business site No Code Backend a B score on the overall speed, with a 94% in performance.



What’s Next?
VTB Solutions and Hostinger have one common mission – giving small to medium-sized enterprises the tools and support to run their businesses. With us, Vitor no longer has to worry about not receiving help when he needs it the most.
“Hostinger’s support is really good and really fast – it’s very different from our previous provider. There, a lot of things happened that I couldn’t even imagine in the first place, that made me have to ask, ‘Why did that happen?’ That’s a big part of why we’re with Hostinger now, and why we probably won’t change, ”said Vitor.
Up next, Vitor will continue to work with his clients and scale his business even further. His ultimate goal is to “democratize software development” using AI so that anyone can build their own solution easily and affordably.
No matter what Vitor needs in his web hosting, our Customer Success team will always be ready to help him.
Source link